NULLCON CTF Web Writeups
Hello everyone!
Today I’m writing my writeup for the CTF Challenges on Nullcon that I’ve done.
Those challenges are all Web related and these are the challenges I’ve done: TYpicalBoss, Debugger, IPfilter, Colorful and Magic Cars.
Let’s see now:
» TYpicalBoss
This was probably the easiest one of all, since I already did some CTFs where PHP Type Juggling was the key to it.
This was the Description of TYpicalBoss Challenge:
My boss just implemented his first PHP website. He mentioned that he managed to calculate a hash that is equal to 0??? I suppose he is not very experienced in PHP yet.
after I read that I looked up at / and there were some files there and one important there was the .db file, I downloaded that file and opened it.
I saw the Hash of the password from admin and already knew what it was about, since I already did PHP Type Juggling challenges.
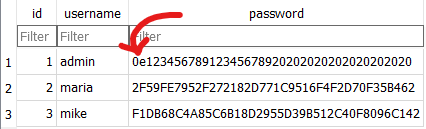
The description and that Hash already made me think it’s gonna be PHP Types, I first tried to find out which hashing algorithm it uses so I could search for a Magic Number/String that could match the Type for that algorithm.
I tried figuring out the hashing algorithm by adding [] to the username/password parameter so I could get an PHP Error/Warning, that it is not an array, I may get some Info like that.
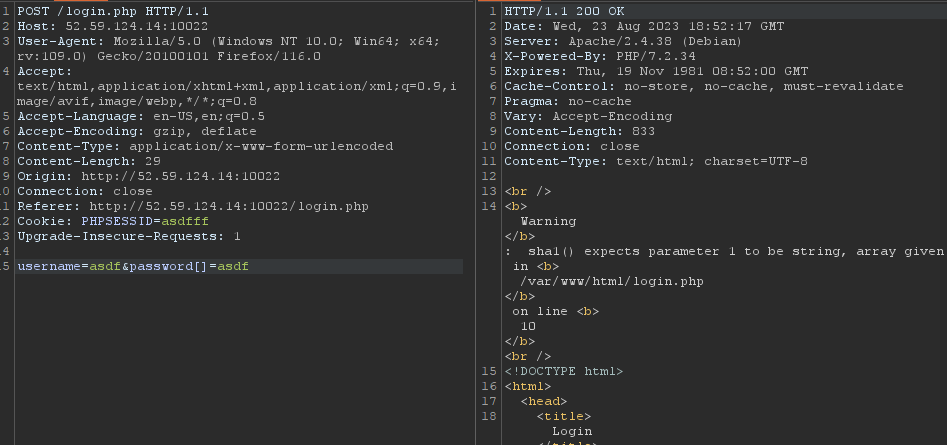
I actually succeded, it’s sha1!
After some Google Search I found this 10932435112 “Magic” Number that should work with sha1 algorithm and guess what, it actually worked.
I got the flag 😁: ENO{m4ny_th1ng5_c4n_g0_wr0ng_1f_y0u_d0nt_ch3ck_typ35}
» Debugger
The next challenge had nothing on the landing page so I first checked the source code
I visited that page and this is the source:
First thing I was focused on was this is_admin check and thought it may have had something to do with some host headers but it didn’t work, later I focused on the whole code
and I noticed the insecure usage of extract(); storing it in debug_info which is later getting loaded, so we could exploit this by using this extract() to overwrite
is_admin to 1, and that’s exatcly what I did.
http://52.59.124.14:10018/?action=debug&filters[is_admin]=1
Another flag: ENO{N3ver_3xtract_ok?}
» IPfilter
This one was the same thing, there was nothing on the landing page, again check the source code and got the URL for Source Code 🙂
A bit longer source, but there are three parameters
bip one is where we are typing the IP and that IP gets fetched + we get the all the information (if we put debug_filter to 1) like it’s shown on that Picture above.
If that IP is not allowed which is for example the IP for backend with secrets 192.168.112.3 or any other IP which is not IPv4 will give you an error message.
We had to bypass it somehow to fetch the 192.168.112.3. I first looked at the regex check:
It’s simple regex, you can type up to 3 numbers there and the first thing I tried was adding a 0 before the 3, so the IP looks like this now: 192.168.112.03
There should be check for 192.168.112.03 and 003 too but there isn’t and it didn’t list it as bad IP
Flag 🥳: ENO{Another_Fl4G_something_IP_STuff!}
» Colorful
This challenge has actually Python source and not PHP, this time the source code was on the landing page, it was quite long source code but the important part is this one here:
If we get admin=1 in our session, then we get the flag. Our session is AES ECB encrypted string of _id={id}&admin={0/1}&color={hexcode}&
id is random generated 8 charachters long hex string.
AES encrypts data in 16 bytes so our admin string gets splited in two halfs, adm and in=0. So we could exploit this since there is no length check on the color parameter.
We get our encrypted cookie and we send the request to the /color/fffffin=1 enpoint, we gather that cookie and we change the placing of our cookie, we add to the previous cookie on the 32
place the 64~till the end - charachters of our cookie from that endpoint and then we just continue our normal cookie with all the left charachters from 32 till 64.
Now we are supposed to have cookie with admin=1 and if we try to visit the page, yes!
Yet another flag: ENO{W3B_H4S_Crypt0!}
» Magic Cars
This is the only challenge till now where we need to download the source code. We have file upload in the gallery there we can only upload GIF.
We need to bypass that in order to upload .php and the bypass was pretty easy %00 just a null byte charachter.
This is how the request looks like, if we visit /images/asdf.php we get the flag!
Last Flag: ENO{4n_uplo4ded_f1l3_c4n_m4k3_wond3r5}